Wide Range Detection of Doublepulsar Implants with Leviathan
As you all know, we published Leviathan Framework 3 days ago. It has limited pool of exploits but we are trying to add new ones. I was checking to find a doublepulsar detection code in Python for implementing it to Leviathan, found a great one: https://github.com/countercept/doublepulsar-detection-script
It's really easy to implement Python exploits to Leviathan by following our manual. I implemented both SMB and RDP codes. So let's see how Leviathan helps you to detect Doublepulsar implants in wide range. This is a great example which shows Leviathan's custom exploit flexibility.
Discovery Phase
Firstly, you need to discover IP addresses which are running RDP or SMB. You have 3 different options:
1)Discover them with Shodan (Auto-query, Manual-query)
1)Discover them with Censys (Auto-query, Manual-query)
1)Discover them with Masscan
For this example, I used Shodan's auto-query feature for detecting RDP services in Turkey (Discovery --> Shodan --> Automatic Query)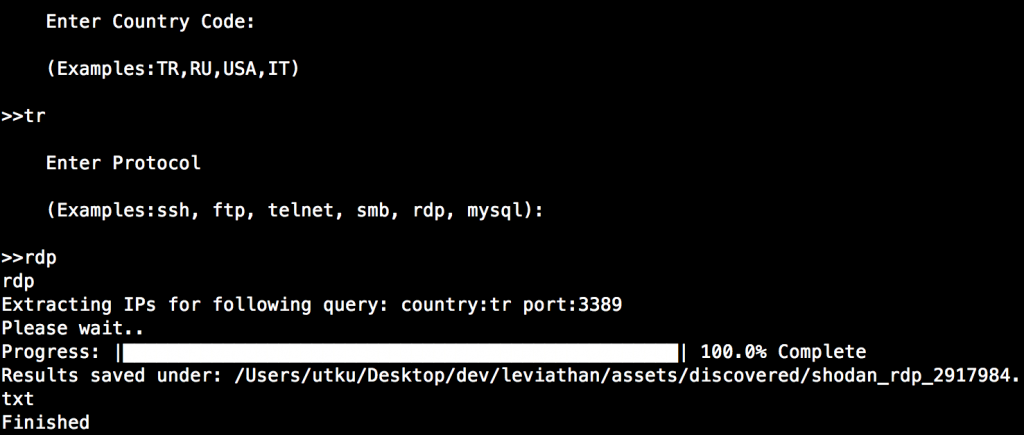
Also, you can use masscan option to discover services in given IP range. This IP range can be the whole Internet :)
Detection
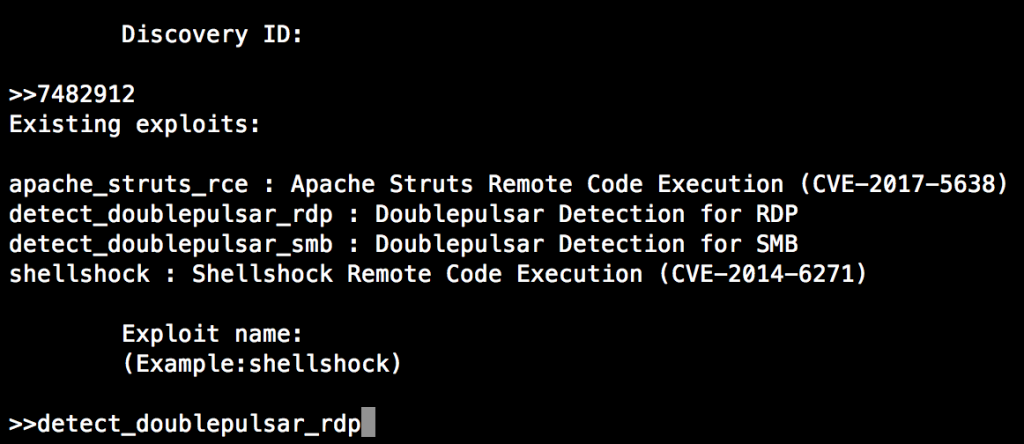
Detection is also easy. Find your discovery id first (Assets --> Show discovered machines --> everything) Copy your discovery id and return back to the main menu.
Go to Custom Exploits section (Attack --> Custom Exploits)
Enter your discovery id, enter the exploit name (detect_doublepulsar_rdp)
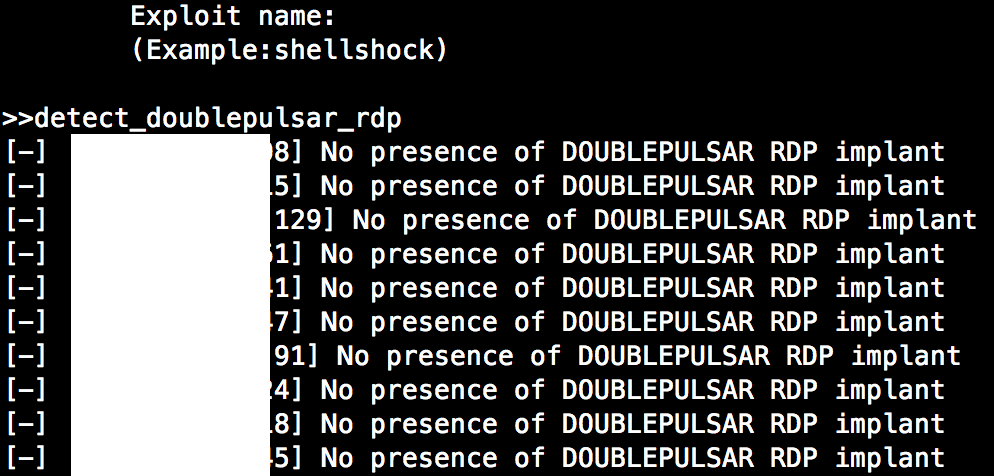
Leviathan will run the exploit against the discovered targets.